PassLeader just published the NEWEST Fortinet NSE7_LED-7.0 exam dumps! And, PassLeader offer two types of the NSE7_LED-7.0 dumps — NSE7_LED-7.0 VCE dumps and NSE7_LED-7.0 PDF dumps, both VCE and PDF contain the NEWEST NSE7_LED-7.0 exam questions, they will help you PASSING the Fortinet NSE7_LED-7.0 exam easily! Now, get the NEWEST NSE7_LED-7.0 dumps in VCE and PDF from PassLeader — https://www.passleader.com/nse7-led-7-0.html (37 Q&As Dumps)
What’s more, part of that PassLeader NSE7_LED-7.0 dumps now are free — https://drive.google.com/drive/folders/1cHmWee-RXeU_93LZejBYl1KQXwVJyGbN
NEW QUESTION 1
Which EAP method requires the use of a digital certificate on both the server end and the client end?
A. EAP-TTLS
B. PEAP
C. EAP-GTC
D. EAP-TLS
Answer: D
Explanation:
According to the FortiGate Administration Guide, “EAP-TLS is the most secure EAP method. It requires a digital certificate on both the server end and the client end. The server and client authenticate each other using their certificates.” Therefore, option D is true because it describes the EAP method that requires the use of a digital certificate on both the server end and the client end. Option A is false because EAP-TTLS only requires a digital certificate on the server end, not the client end. Option B is false because PEAP also only requires a digital certificate on the server end, not the client end. Option C is false because EAP-GTC does not require a digital certificate on either the server end or the client end.
NEW QUESTION 2
Which two statements about the MAC-based 802.1X security mode available on FortiSwitch are true? (Choose two.)
A. FortiSwitch authenticates a single device and opens the port to other devices connected to the port.
B. FortiSwitch authenticates each device connected to the port.
C. It cannot be used in conjunction with MAC authentication bypass.
D. FortiSwitch can grant different access levels to each device connected to the port.
Answer: BD
Explanation:
According to the FortiSwitch Administration Guide, “MAC-based 802.1X security mode allows you to authenticate each device connected to a port using its MAC address as the username and password.” Therefore, option B is true because it describes the MAC-based 802.1X security mode available on FortiSwitch. Option D is also true because FortiSwitch can grant different access levels to each device connected to the port based on the user group and security policy assigned to them. Option A is false because FortiSwitch does not authenticate a single device and open the port to other devices connected to the port, but rather authenticates each device individually. Option C is false because MAC-based 802.1X security mode can be used in conjunction with MAC authentication bypass (MAB) or EAP pass-through modes, which are fallback options for non-802.1X devices.
NEW QUESTION 3
When you configure a FortiAP wireless interface for auto TX power control, which statement describes how it configures its transmission power?
A. Every 30 seconds the AP will measure the signal strength of the AP using the client. The AP will adjust its signal strength up or down until the AP signal is detected at -70 dBm.
B. Every 30 seconds FortiGate measures the signal strength of adjacent AP interfaces. It will adjust its own AP power to match the adjacent AP signal strength.
C. Every 30 seconds FortiGate measures the signal strength of adjacent FortiAP interfaces. It will adjust the adjacent AP power to be detectable at -70 dBm.
D. Every 30 seconds FortiGate measures the signal strength of the weakest associated client. The AP will then configure its radio power to match the detected signal strength of the client.
Answer: A
Explanation:
According to the FortiAP Configuration Guide, “Auto TX power control allows the AP to adjust its transmit power based on the signal strength of the client. The AP will measure the signal strength of the client every 30 seconds and adjust its transmit power up or down until the client signal is detected at -70 dBm.” Therefore, option A is true because it describes how the FortiAP wireless interface configures its transmission power when auto TX power control is enabled. Option B is false because FortiGate does not measure the signal strength of adjacent AP interfaces, but rather the FortiAP does. Option C is false because FortiGate does not adjust the adjacent AP power, but rather the FortiAP adjusts its own power. Option D is false because FortiGate does not measure the signal strength of the weakest associated client, but rather the FortiAP does.
NEW QUESTION 4
An administrator has configured an SSID in bridge mode for corporate employees. All APs are online and provisioned using default AP profiles. Employees are unable to locate the SSID to conned. Which two configurations can the administrator verify? (Choose two.)
A. Verify that the broadcast SSID option is enabled in the SSID configuration.
B. Verify that the Block Intra-SSID Traffic (intra-vap-privacy) option in the SSID configuration is disabled.
C. Verify that the SSID to an AP group that should be broadcasting the SSID is applied.
D. Verify that the SSID is manually applied on AP profiles for both 2.4 GHz and 5 GHz radios.
Answer: AC
Explanation:
According to the FortiAP Configuration Guide, “To enable the SSID, you must select at least one channel for the radio. If no channels are selected, the SSID will not be enabled. You must also enable Broadcast SSID.” Therefore, option A is true because the broadcast SSID option allows the SSID to be visible to wireless clients. Option C is also true because the SSID must be applied to an AP group that contains the APs that should be broadcasting the SSID. According to the same guide, “You can create AP groups and assign them to different locations or departments. You can then apply different settings, such as SSIDs, to each group.” Option B is false because blocking intra-SSID traffic prevents wireless clients on the same SSID from communicating with each other, which is not related to broadcasting the SSID. Option D is false because the SSID can be applied to an AP group or a global profile, which will automatically apply to all APs, without manually configuring each AP profile.
NEW QUESTION 5
What is the purpose of enabling Windows Active Directory Domain Authentication on FortiAuthenticator?
A. It enables FortiAuthenticator to use Windows administrator credentials to perform an LDAP lookup for a user search.
B. It enables FortiAuthenticator to use a Windows CA certificate when authenticating RADIUS users.
C. It enables FortiAuthenticator to import users from Windows AD.
D. It enables FortiAuthenticator to register itself as a Windows trusted device to proxy authentication using Kerberos.
Answer: D
Explanation:
According to the FortiAuthenticator Administration Guide, “Windows Active Directory domain authentication enables FortiAuthenticator to join a Windows Active Directory domain as a machine entity and proxy authentication requests using Kerberos.” Therefore, option D is true because it describes the purpose of enabling Windows Active Directory domain authentication on FortiAuthenticator. Option A is false because FortiAuthenticator does not need Windows administrator credentials to perform an LDAP lookup for a user search. Option B is false because FortiAuthenticator does not use a Windows CA certificate when authenticating RADIUS users, but rather its own CA certificate. Option C is false because FortiAuthenticator does not import users from Windows AD, but rather synchronizes them using LDAP or FSSO.
NEW QUESTION 6
You are configuring a FortiGate wireless network to support automated wireless client quarantine using IOC. Which two configurations must you put in place for a wireless client to be quarantined successfully? (Choose two.)
A. Configure the wireless network to be in tunnel mode.
B. Configure the FortiGate device in the Security Fabric with a FortiAnalyzer device.
C. Configure a firewall policy to allow communication.
D. Configure the wireless network to be in bridge mode.
Answer: AB
Explanation:
According to the FortiGate Administration Guide, “To enable automated wireless client quarantine using IOC, you must configure the following settings: Configure your wireless network to be in tunnel mode. This allows FortiGate to inspect all wireless traffic and apply security policies. Configure your FortiGate device in the Security Fabric with a FortiAnalyzer device. This allows FortiAnalyzer to detect indicators of compromise (IOC) from wireless traffic and send quarantine commands to FortiGate.” Therefore, options A and B are true because they describe the configurations that must be put in place for a wireless client to be quarantined successfully using IOC. Option C is false because configuring a firewall policy to allow communication is not required, as the default firewall policy for tunnel mode wireless networks is to allow all traffic. Option D is false because configuring the wireless network to be in bridge mode is not supported, as FortiGate cannot inspect or quarantine wireless traffic in bridge mode.
NEW QUESTION 7
Which two statements about FortiSwitch manager are true? (Choose two.)
A. Per-device management is the default management mode on FortiManager.
B. FortiManager obtains the FortiSwitch status information by querying the FortiGate REST API every three minutes.
C. If the administrator makes any changes on FortiSwitch manager they must also install those changes on FortiGate so that those changes are applied on the managed switches.
D. Any switch discovered or authorized on FortiGate must be added manually on FortiSwitch manager.
Answer: BC
Explanation:
According to the FortiManager Administration Guide, “FortiManager obtains the FortiSwitch status information by querying the FortiGate REST API every three minutes.” Therefore, option B is true because it describes how FortiManager gets the information about the managed switches. According to the same guide2, “If you make any changes in this module, you must install them on your managed device so that they are applied on your managed switches.” Therefore, option C is true because it describes what the administrator must do after making any changes on FortiSwitch manager. Option A is false because central management is the default management mode on FortiManager, not per-device management. Option D is false because any switch discovered or authorized on FortiGate will be automatically added on FortiSwitch manager, not manually.
NEW QUESTION 8
A wireless network in a school provides guest access using a captive portal to allow unregistered users to self-register and access the network. The administrator is requested to update the existing configuration to provide captive portal authentication through a secure connection (HTTPS). Which two changes must the administrator make to enforce HTTPS authentication? (Choose two.)
A. Create a new SSID with the HTTPS captive portal URL.
B. Enable HTTP redirect in the user authentication settings.
C. Disable HTTP administrative access on the guest SSID to enforce HTTPS connection.
D. Update the captive portal URL to use HTTPS on FortiGate and FortiAuthenticator.
Answer: BD
Explanation:
According to the FortiGate Administration Guide, “To enable HTTPS authentication, you must enable HTTP redirect in the user authentication settings. This redirects HTTP requests to HTTPS. You must also update the captive portal URL to use HTTPS on both FortiGate and FortiAuthenticator.” Therefore, options B and D are true because they describe the changes that the administrator must make to enforce HTTPS authentication for the captive portal. Option A is false because creating a new SSID with the HTTPS captive portal URL is not required, as the existing SSID can be updated with the new URL. Option C is false because disabling HTTP administrative access on the guest SSID will not enforce HTTPS connection, but rather block HTTP connection.
NEW QUESTION 9
Which two pieces of information can the diagnose test authserver ldap command provide? (Choose two.)
A. It displays whether the admin bind user credentials are correct.
B. It displays whether the user credentials are correct.
C. It displays the LDAP codes returned by the LDAP server.
D. It displays the LDAP groups found for the user.
Answer: BC
Explanation:
According to the FortiGate CLI Reference Guide, “The diagnose test authserver ldap command tests LDAP authentication with a specific LDAP server. The command displays whether the user credentials are correct and whether the user belongs to any groups that match a firewall policy. The command also displays the LDAP codes returned by the LDAP server.” Therefore, options B and C are true because they describe the information that the diagnose test authserver ldap command can provide. Option A is false because the command does not display whether the admin bind user credentials are correct, but rather whether the user credentials are correct. Option D is false because the command does not display the LDAP groups found for the user, but rather whether the user belongs to any groups that match a firewall policy.
NEW QUESTION 10
You are setting up an SSID (VAP) to perform RADlUS-authenticated dynamic VLAN allocation. Which three RADIUS attributes must be supplied by the RADIUS server to enable successful VLAN allocation? (Choose three.)
A. Tunnel-Private-Group-ID
B. Tunnel-Pvt-Group-ID
C. Tunnel-Preference
D. Tunnel-Type
E. Tunnel-Medium-Type
Answer: ADE
Explanation:
According to the FortiAP Configuration Guide, “To perform RADIUS-authenticated dynamic VLAN allocation, the RADIUS server must supply the following RADIUS attributes: Tunnel-Private-Group-ID, which specifies the VLAN ID to assign to the user. Tunnel-Type, which specifies the tunneling protocol used for the VLAN. The value must be 13 (VLAN). Tunnel-Medium-Type, which specifies the transport medium used for the VLAN. The value must be 6 (802). Therefore, options A, D, and E are true because they describe the RADIUS attributes that must be supplied by the RADIUS server to enable successful VLAN allocation. Option B is false because Tunnel-Pvt-Group-ID is not a valid RADIUS attribute name, but rather a typo for Tunnel-Private-Group-ID. Option C is false because Tunnel- Preference is not a required RADIUS attribute for dynamic VLAN allocation, but rather an optional attribute that specifies the priority of the VLAN.
NEW QUESTION 11
Which two statements about MAC address quarantine by redirect mode are true? (Choose two.)
A. The quarantined device is moved to the quarantine VLAN.
B. The device MAC address is added to the Quarantined Devices firewall address group.
C. It is the default mode for MAC address quarantine.
D. The quarantined device is kept in the current VLAN.
Answer: BD
Explanation:
According to the FortiGate Administration Guide, “MAC address quarantine by redirect mode allows you to quarantine devices by adding their MAC addresses to a firewall address group called Quarantined Devices. The quarantined devices are kept in their current VLANs, but their traffic is redirected to a quarantine portal.” Therefore, options B and D are true because they describe the statements about MAC address quarantine by redirect mode. Option A is false because the quarantined device is not moved to the quarantine VLAN, but rather kept in the current VLAN. Option C is false because redirect mode is not the default mode for MAC address quarantine, but rather an alternative mode that can be enabled by setting mac-quarantine-mode to redirect.
NEW QUESTION 12
Refer to the exhibit:
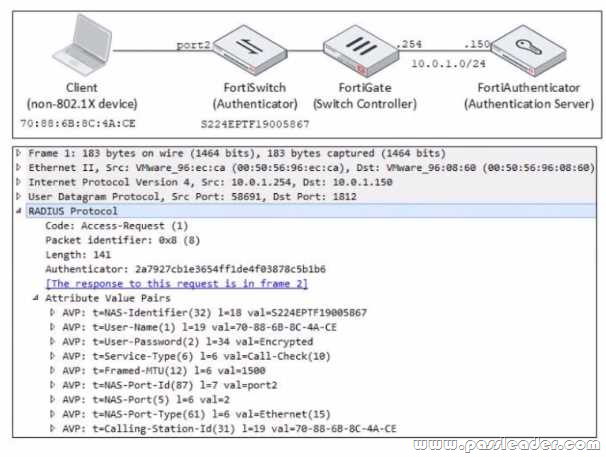
Examine the network diagram and packet capture shown in the exhibit. The packet capture was taken between FortiGate and FortiAuthenticator and shows a RADIUS Access-Request packet sent by FortiSwitch to FortiAuthenticator through FortiGate. Why does the User-Name attribute in the RADIUS Access-Request packet contain the client MAC address?
A. The client is performing AD machine authentication.
B. FortiSwitch is authenticating the client using MAC authentication bypass.
C. The client is performing user authentication.
D. FortiSwitch is sending a RADIUS accounting message to FortiAuthenticator.
Answer: B
Explanation:
According to the exhibit, the User-Name attribute in the RADIUS Access-Request packet contains the client MAC address of 00:0c:29:6a:2b:3d. This indicates that FortiSwitch is authenticating the client using MAC authentication bypass (MAB), which is a method of authenticating devices that do not support 802.1X by using their MAC address as the username and password. Therefore, option B is true because it explains why the User-Name attribute contains the client MAC address. Option A is false because AD machine authentication uses a computer account name and password, not a MAC address. Option C is false because user authentication uses a user name and password, not a MAC address. Option D is false because FortiSwitch is sending a RADIUS Access-Request message to FortiAuthenticator, not a RADIUS accounting message.
NEW QUESTION 13
Refer to the exhibit:
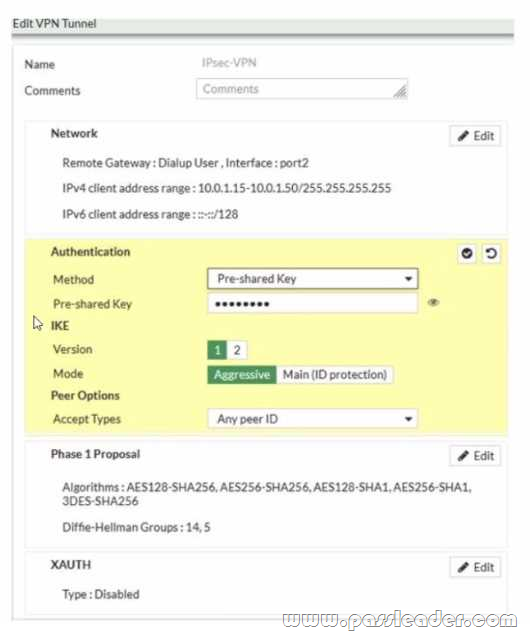
Examine the IPsec VPN phase 1 configuration shown in the exhibit. An administrator wants to use certificate-based authentication for an IPsec VPN user. Which three configuration changes must you make on FortiGate to perform certificate-based authentication for the IPsec VPN user? (Choose three.)
A. Create a PKI user for the IPsec VPN user, and then configure the IPsec VPN tunnel to accept the PKI user as peer certificate.
B. In the Authentication section of the IPsec VPN tunnel in the Method drop-down list select Signature and then select the certificate that FortiGate will use for IPsec VPN.
C. In the IKE section of the IPsec VPN tunnel in the Mode field select Main (ID protection).
D. Import the CA that signed the user certificate.
E. Enable XAUTH on the IPsec VPN tunnel.
Answer: BDE
Explanation:
According to the FortiGate Administration Guide, “To use certificate-based authentication, you must configure the following settings on both peers: Select Signature as the authentication method and select a certificate to use for authentication. Import the CA certificate that issued the peer’s certificate. Enable XAUTH on the phase 1 configuration.” Therefore, options B, D, and E are true because they describe the configuration changes that must be made on FortiGate to perform certificate-based authentication for the IPsec VPN user. Option A is false because creating a PKI user for the IPsec VPN user is not required, as the user certificate can be verified by the CA certificate. Option C is false because changing the IKE mode to Main (ID protection) is not required, as the IKE mode can be either Main or Aggressive for certificate-based authentication.
NEW QUESTION 14
Refer to the exhibit:
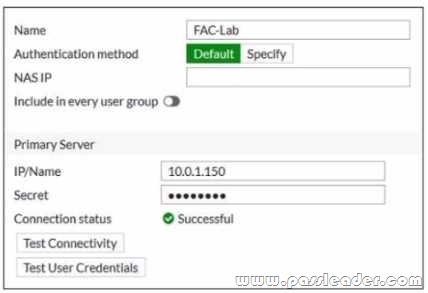
Examine the RADIUS server configuration shown in the exhibit. An administrator has configured a RADIUS server on FortiGate that points to FortiAuthenticator FortiAuthenticator is acting as an authentication proxy and is configured to relay all authentication requests to a remote Windows AD server using LDAP. While testing the configuration the administrator noticed that the diagnose test authserver command worked with PAP, however authentication requests failed when using MSCHAP2. Which two solutions can the administrator implement to get MSCHAP2 authentication to work? (Choose two.)
A. On FortiAuthenticator enable Windows Active Directory Domain Authentication to add FortiAuthenticator to the Windows domain.
B. On FortiGate configure the NAS IP setting on the RADIUS server.
C. On FortiAuthenticator change the back-end authentication server from LDAP to RADIUS.
D. On FortiGate update the Secret setting on the RADIUS server.
Answer: AC
Explanation:
According to the exhibit, the RADIUS server configuration on FortiGate points to FortiAuthenticator, which is acting as an authentication proxy and is configured to relay all authentication requests to a remote Windows AD server using LDAP. However, LDAP does not support MSCHAP2 authentication, which is required for RADIUS. Therefore, option A is true because on FortiAuthenticator, enabling Windows Active Directory Domain Authentication will add FortiAuthenticator to the Windows domain and allow it to use MSCHAP2 authentication with the AD server. Option C is also true because on FortiAuthenticator, changing the back-end authentication server from LDAP to RADIUS will allow it to use MSCHAP2 authentication with the AD server. Option B is false because on FortiGate, configuring the NAS IP setting on the RADIUS server will not affect the MSCHAP2 authentication, but rather the source IP address of the RADIUS packets. Option D is false because on FortiGate, updating the Secret setting on the RADIUS server will not affect the MSCHAP2 authentication, but rather the shared secret between FortiGate and FortiAuthenticator.
NEW QUESTION 15
Refer to the exhibit showing a network topology and SSID settings:
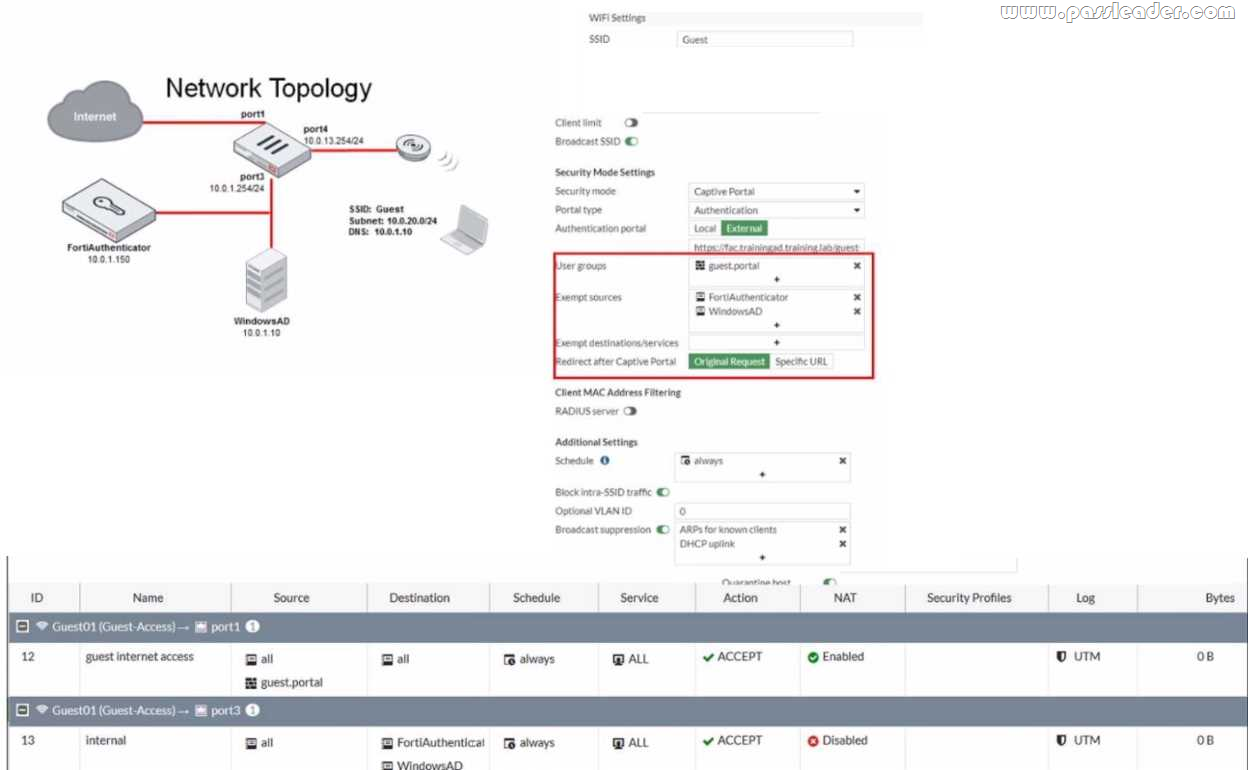
FortiGate is configured to use an external captive portal. However wireless users are not able to see the captive portal login page. Which configuration change should the administrator make to fix the problem?
A. Enable NAT in the firewall policy with the ID 13.
B. Add the FortiAuthenticator and WindowsAD address objects as exempt destinations services.
C. Enable the captive-portal-exempt option in the firewall policy with the ID 12.
D. Remove the guest.portal user group in the firewall policy with the ID 12.
Answer: B
Explanation:
According to the exhibit, the network topology and SSID settings show that FortiGate is configured to use an external captive portal hosted on FortiAuthenticator, which is connected to a Windows AD server for user authentication. However, wireless users are not able to see the captive portal login page, which means that they are not redirected to the external captive portal URL. Therefore, option B is true because adding the FortiAuthenticator and WindowsAD address objects as exempt destinations services will allow the wireless users to access the external captive portal URL without being blocked by the firewall policy. Option A is false because enabling NAT in the firewall policy with the ID 13 will not affect the redirection to the external captive portal URL, but rather the source IP address of the wireless traffic. Option C is false because enabling the captive-portal-exempt option in the firewall policy with the ID 12 will bypass the captive portal authentication for the wireless users, which is not the desired outcome. Option D is false because removing the guest.portal user group in the firewall policy with the ID 12 will prevent the wireless users from being authenticated by FortiGate, which is required for accessing the external captive portal.
NEW QUESTION 16
……
Learning the PassLeader NSE7_LED-7.0 dumps with VCE and PDF for 100% passing Fortinet certification — https://www.passleader.com/nse7-led-7-0.html (37 Q&As Dumps)
BONUS!!! Download part of PassLeader NSE7_LED-7.0 dumps for free — https://drive.google.com/drive/folders/1cHmWee-RXeU_93LZejBYl1KQXwVJyGbN