PassLeader just published the NEWEST Fortinet FCP_FGT_AD-7.6 exam dumps! And, PassLeader offer two types of the FCP_FGT_AD-7.6 dumps — FCP_FGT_AD-7.6 VCE dumps and FCP_FGT_AD-7.6 PDF dumps, both VCE and PDF contain the NEWEST FCP_FGT_AD-7.6 exam questions, they will help you PASSING the Fortinet FCP_FGT_AD-7.6 exam easily! Now, get the NEWEST FCP_FGT_AD-7.6 dumps in VCE and PDF from PassLeader — https://www.passleader.com/fcp-fgt-ad-7-6.html (130 Q&As Dumps)
What’s more, part of that PassLeader FCP_FGT_AD-7.6 dumps now are free — https://drive.google.com/drive/folders/1l2Xp4fmvZPw4KvHCmy14sKNV0J5qfpAW
NEW QUESTION 106
An administrator must enable a DHCP server on one of the directly connected networks on FortiGate. However, the administrator is unable to complete the process on the GUI to enable the service on the interface. In this scenario, what prevents the administrator from enabling DHCP service?
A. The DHCP server setting is available only on the CLI.
B. Another interface is configured as the only DHCP server on FortiGate.
C. The FortiGate model does not support the DHCP server.
D. The role of the interface prevents setting a DHCP server.
Answer: D
Explanation:
An interface’s role (for example, WAN or DMZ) determines whether DHCP server configuration is allowed. If the interface is set to a role such as WAN, FortiGate restricts enabling DHCP server service on that interface. To enable DHCP, the interface role must be changed to LAN or Internal, which supports DHCP server functionality.
NEW QUESTION 107
Which two statements describe how the RPF check is used? (Choose two.)
A. The RPF check is a mechanism that protects FortiGate and the network from IP spoofing attacks.
B. The RPF check is run on the first reply packet of any new session.
C. The RPF check is run on the first sent packet of any new session.
D. The RPF check is run on the first sent and reply packet of any new session.
Answer: AC
Explanation:
The RPF (Reverse Path Forwarding) check is used to prevent IP spoofing attacks by verifying that the source IP address of a received packet is reachable through the same interface it arrived on. If not, the packet is dropped, ensuring traffic legitimacy. The RPF check runs on the first sent packet of any new session to validate that the route to the source IP is consistent with the interface it’s received on. This helps FortiGate detect spoofed or asymmetric routing scenarios early in the session establishment.
NEW QUESTION 108
Which two settings are required for SSL VPN to function between two FortiGate devices? (Choose two.)
A. The server FortiGate requires a CA certificate to verify the client FortiGate certificate.
B. The client FortiGate requires a manually added route to remote subnets.
C. The client FortiGate requires a client certificate signed by the CA on the server FortiGate.
D. The client FortiGate requires the SSL VPN tunnel interface type to connect SSL VPN.
Answer: AC
Explanation:
– The server FortiGate requires a CA certificate to verify the client FortiGate certificate.
When configuring an SSL VPN tunnel between two FortiGates, the server FortiGate must verify the authenticity of the connecting client’s certificate. This is done using a CA certificate installed on the server to ensure the client certificate is trusted.
– The client FortiGate requires a client certificate signed by the CA on the server FortiGate.
The client FortiGate uses this client certificate to authenticate itself to the server during SSL VPN negotiation. The certificate must be signed by the same CA trusted by the server to establish a secure, validated SSL VPN connection.
NEW QUESTION 109
A network administrator is configuring an IPsec VPN tunnel for a sales employee travelling abroad. Which IPsec Wizard template must the administrator apply?
A. Hub-and-Spoke
B. Site to Site
C. Remote Access
D. Dial up User
Answer: C
Explanation:
The Remote Access IPsec Wizard template is used for individual users connecting from remote locations, such as traveling employees. This template configures FortiGate to act as an IPsec VPN server, allowing remote clients (like FortiClient) to securely connect and access internal network resources while abroad.
NEW QUESTION 110
Which statement is a characteristic of automation stitches?
A. They can have one or more triggers.
B. They can be created only on downstream devices in the fabric.
C. They can run multiple actions at the same time.
D. They can be run only on devices in the Security Fabric.
Answer: A
Explanation:
Automation stitches in FortiGate are event-driven workflows that can include one or more triggers and one or more actions. Triggers define the condition that starts the stitch (for example, a failed login or a system event), while actions define what FortiGate should do in response (such as sending an alert or executing a script).
NEW QUESTION 111
Which three methods are used by the collector agent for AD polling? (Choose three.)
A. WinSecLog
B. NetAPI
C. FortiGate Polling
D. FSSO REST API
E. WMI
Answer: BDE
Explanation:
The Fortinet Collector Agent can use the following methods to poll Active Directory (AD) for user logon events:
* NetAPI – Queries the domain controllers directly to obtain user logon information.
* FSSO REST API – Allows integration and polling via modern API-based communication for user authentication updates.
* WMI (Windows Management Instrumentation) – Retrieves logon data from domain controllers using WMI queries.
NEW QUESTION 112
An employee needs to connect to the office through a high-latency internet connection. Which SSL VPN setting should the administrator adjust to prevent SSL VPN negotiation failure?
A. SSL VPN dtls-hello-timeout.
B. SSL VPN login-timeout.
C. SSL VPN session-ttl.
D. SSL VPN idle-timeout.
Answer: B
Explanation:
The SSL VPN login-timeout setting defines how long FortiGate waits for a client to complete the SSL VPN negotiation process. On high-latency connections, the negotiation may take longer than usual. Increasing the login-timeout value prevents the VPN session from failing during the initial connection phase.
NEW QUESTION 113
FortiGate is integrated with FortiAnalyzer and FortiManager. When a firewall policy is created, which attribute is added to the policy to improve functionality and to support recording logs to FortiAnalyzer or FortiManager?
A. Sequence ID
B. Log ID
C. Policy ID
D. Universally Unique Identifier
Answer: D
Explanation:
When FortiGate is integrated with FortiAnalyzer or FortiManager, each firewall policy is assigned a Universally Unique Identifier (UUID). This UUID allows consistent identification and tracking of the policy across devices and log systems, even if the policy ID changes. It ensures accurate correlation of logs and centralized management across Fortinet’s management and analysis platforms.
NEW QUESTION 114
Which method allows management access to the FortiGate CLI without network connectivity?
A. CLI console widget.
B. SSH console.
C. Telnet console.
D. Serial console.
Answer: D
Explanation:
The serial console provides direct physical access to the FortiGate CLI without requiring any network connectivity. It connects via the FortiGate’s console port using a serial cable, allowing administrators to perform initial configuration, recovery, or troubleshooting even if the network interfaces are down or misconfigured.
NEW QUESTION 115
Which inspection mode does FortiGate use for application profiles if it is configured as a profile-based next-generation firewall (NGFW)?
A. Certificate inspection.
B. Flow-based inspection.
C. Proxy-based inspection.
D. Full content inspection.
Answer: C
Explanation:
When FortiGate operates in profile-based NGFW mode, it supports both flow-based and proxy-based inspection for security profiles. However, application profiles (such as Application Control, Web Filter, and Antivirus) are inspected using proxy-based inspection by default in profile-based mode, as this mode allows FortiGate to fully analyze and enforce policies on the application content layer.
NEW QUESTION 116
Which two features of IPsec IKEv1 authentication are supported by FortiGate? (Choose two.)
A. Extended authentication (XAuth) for faster authentication because fewer packets are exchanged.
B. Pre-shared key and certificate signature as authentication methods.
C. No certificate is required on the remote peer when you set the certificate signature as the authentication method.
D. Extended authentication (XAuth) to request the remote peer to provide a username and password.
Answer: BD
Explanation:
– Pre-shared key and certificate signature as authentication methods.
FortiGate supports both pre-shared keys and digital certificates for IKEv1 authentication, providing flexibility in securing IPsec VPN tunnels.
– Extended authentication (XAuth) to request the remote peer to provide a username and password.
FortiGate supports XAuth in IKEv1 to add an extra layer of user-level authentication, where the remote peer must provide a username and password in addition to the IKE credentials.
NEW QUESTION 117
An administrator manages a FortiGate model that supports NTurbo. How does NTurbo enhance performance for flow-based inspection?
A. NTurbo buffers the whole file and then sends it to the antivirus engine.
B. NTurbo creates a special data path to redirect traffic between the IPS engine its ingress and egress interfaces.
C. NTurbo creates two inspection sessions on the FortiGate device.
D. NTurbo offloads traffic to the content processor.
Answer: B
Explanation:
NTurbo enhances flow-based inspection performance by creating a fast data path between the IPS engine and the ingress/egress interfaces. This allows traffic to be inspected efficiently without needing to pass through the slower, traditional packet path, thus reducing CPU load and improving throughput during flow-based security inspections.
NEW QUESTION 118
The HTTP inspection process in web filtering follows a specific order when multiple features are enabled in the web filter profile. Which order must FortiGate use when the web filter profile has features such as safe search enabled?
A. DNS-based web filter and proxy-based web filter.
B. Static URL filter, FortiGuard category filter, and advanced filters.
C. FortiGuard category filter and rating filter.
D. Static domain filter, SSL inspection filter, and external connectors filters.
Answer: B
Explanation:
When multiple web filtering features are enabled, FortiGate processes HTTP inspection in the following order:
1. Static URL filter: checks requests against manually configured URLs or patterns.
2. FortiGuard category filter: classifies the website based on FortiGuard’s web reputation and category database.
3. Advanced filters: applies additional options such as safe search enforcement, YouTube restriction, and keyword filtering.
NEW QUESTION 119
Refer to the exhibit:
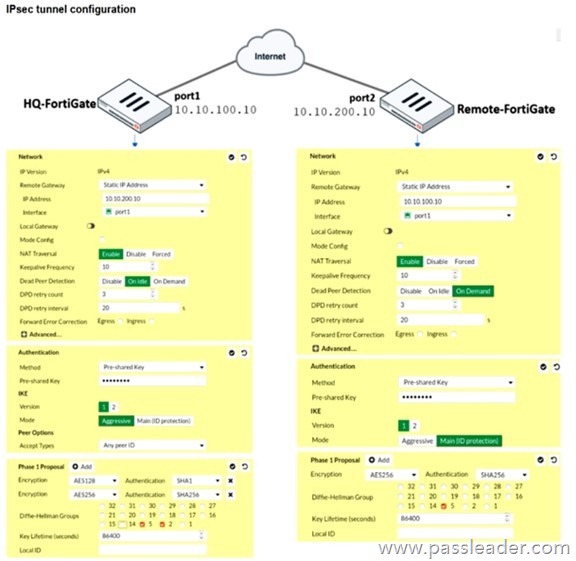
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 failed to come up. The administrator has also re-entered the pre-shared key on both FortiGate devices to make sure they match. Based on the phase 1 configuration and the diagram shown in the exhibit, which two configuration changes can the administrator make to bring phase 1 up? (Choose two.)
A. On HQ-FortiGate, set IKE mode to Main (ID protection).
B. On Remote-FortiGate, set port2 as Interface.
C. On HQ-FortiGate, disable Diffie-Helman group 2.
D. On both FortiGate devices, set Dead Peer Detection to On Demand.
Answer: AB
Explanation:
– On the HQ-FortiGate, the IKE phase 1 mode is set to Aggressive, while on the Remote-FortiGate it is set to Main (ID protection). Both sides must use the same IKE mode for phase 1 to come up, so changing HQ-FortiGate to Main mode resolves this mismatch.
– On the Remote-FortiGate, the phase 1 Interface is configured as port1, but according to the diagram the WAN-facing interface with IP 10.10.200.10 is port2. The local interface in the IPsec configuration must match the physical WAN interface, so changing it to port2 is required for the tunnel to establish.
NEW QUESTION 120
Refer to the exhibit to view the firewall policy:
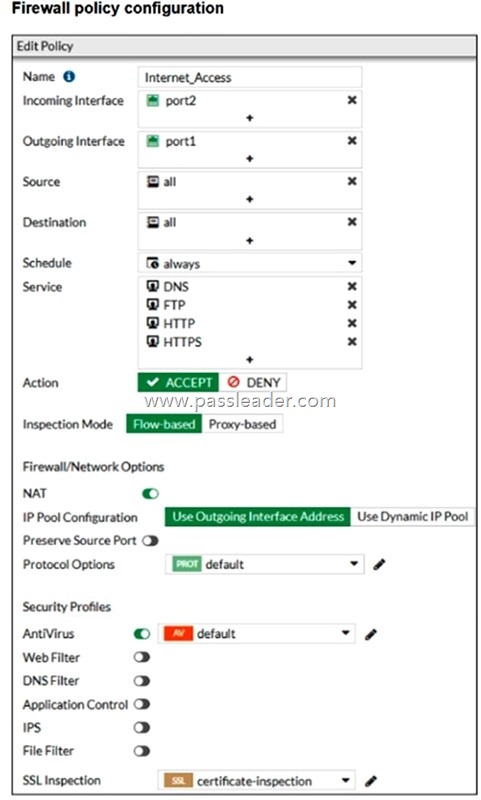
Why would the firewall policy not block a well-known virus, for example eicar?
A. The firewall policy does not apply deep content inspection.
B. Web filter is not enabled on the firewall policy to complement the antivirus profile.
C. The firewall policy is not configured in proxy-based inspection mode.
D. The action on the firewall policy is not set to deny.
Answer: A
Explanation:
The firewall policy uses certificate-inspection under SSL inspection and flow-based inspection mode. Certificate inspection does not decrypt HTTPS traffic; it only checks the certificate fields. Because of this, FortiGate cannot perform deep content inspection, which is required for antivirus to detect and block threats such as the EICAR test virus within encrypted HTTPS sessions.
NEW QUESTION 121
Refer to the exhibit:
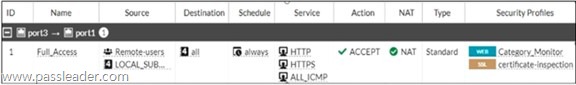
FortiGate is configured for firewall authentication. When attempting to access an external website, the user is not presented with a login prompt. What is the most likely reason for this situation?
A. The Service DNS is required in the firewall policy.
B. The user is using an incorrect user name.
C. No matching user account exists for this user.
D. The Remote-users group is not added to the Destination.
Answer: A
Explanation:
In FortiGate firewall authentication, users are prompted for login credentials only when their initial request matches a policy requiring authentication. In this configuration, the firewall policy permits HTTP, HTTPS, and ICMP traffic, but DNS service is missing. Since browsers first need DNS resolution before sending HTTP/HTTPS requests, the user cannot reach the FortiGate for authentication. Adding DNS to the Service field (Option A) enables the user to resolve hostnames and trigger the firewall authentication prompt.
NEW QUESTION 122
Refer to the exhibit, which shows the IPS sensor configuration:
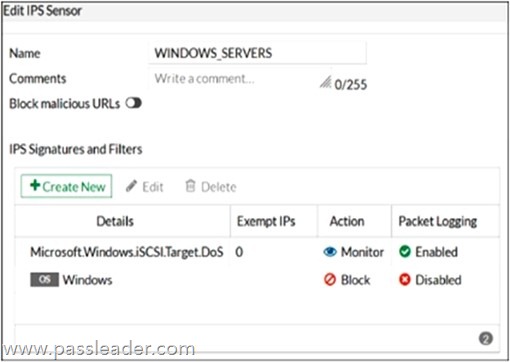
If traffic matches this IPS sensor, which two actions is the sensor expected to take? (Choose two.)
A. The sensor will reset all connections that match these signatures.
B. The sensor will gather a packet log for all matched traffic.
C. The sensor will allow attackers matching the Microsoft.Windows.iSCSI.Target.DoS signature.
D. The sensor will block all attacks aimed at Windows servers.
Answer: CD
Explanation:
– The sensor will allow attackers matching the Microsoft.Windows.iSCSITarget.DoS signature.
The action for this specific signature is set to Monitor, which means FortiGate will only detect and log the activity but will not block or reset the session.
– The sensor will block all attacks aimed at Windows servers.
The general Windows filter is configured with the Block action, so any traffic matching Windows-related attack signatures will be blocked.
NEW QUESTION 123
Refer to the exhibit:
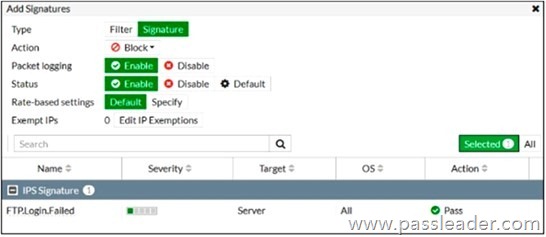
Review the intrusion prevention system (IPS) profile signature settings shown in the exhibit. What do you conclude when adding the FTP.Login.Failed signature to the IPS sensor profile?
A. Traffic matching the signature will be allowed and logged.
B. The signature setting uses a custom rating threshold.
C. The signature setting includes a group of other signatures.
D. Traffic matching the signature will be silently dropped and logged.
Answer: A
Explanation:
In the exhibit, the FTP.Login.Failed IPS signature has the Action set to Pass and Packet Logging enabled. The traffic matching this signature will not be blocked; instead, it will be allowed (passed) through the FortiGate. Because packet logging is enabled, the matching events will be logged for monitoring or analysis.
NEW QUESTION 124
……
Learning the PassLeader FCP_FGT_AD-7.6 dumps with VCE and PDF for 100% passing Fortinet certification — https://www.passleader.com/fcp-fgt-ad-7-6.html (130 Q&As Dumps)
BONUS!!! Download part of PassLeader FCP_FGT_AD-7.6 dumps for free — https://drive.google.com/drive/folders/1l2Xp4fmvZPw4KvHCmy14sKNV0J5qfpAW