PassLeader just published the NEWEST Fortinet FCP_FSM_AN-7.2 exam dumps! And, PassLeader offer two types of the FCP_FSM_AN-7.2 dumps — FCP_FSM_AN-7.2 VCE dumps and FCP_FSM_AN-7.2 PDF dumps, both VCE and PDF contain the NEWEST FCP_FSM_AN-7.2 exam questions, they will help you PASSING the Fortinet FCP_FSM_AN-7.2 exam easily! Now, get the NEWEST FCP_FSM_AN-7.2 dumps in VCE and PDF from PassLeader — https://www.passleader.com/fcp-fsm-an-7-2.html (42 Q&As Dumps)
What’s more, part of that PassLeader FCP_FSM_AN-7.2 dumps now are free — https://drive.google.com/drive/folders/1N_fTofCvnsvQtf81GrH6Zts-VjBXOe2Y
NEW QUESTION 1
What can you use to send data to FortiSIEM for user and entity behavior analytics (UEBA)?
A. FortiSIEM agent.
B. SSH.
C. SNMP.
D. FortiSIEM worker.
Answer: A
Explanation:
The FortiSIEM agent can be used to send detailed endpoint data such as user activity and process behavior to FortiSIEM, which is essential for performing User and Entity Behavior Analytics (UEBA).
NEW QUESTION 2
Which items are used to define a subpattern?
A. Filters, Aggregate, Group By definitions.
B. Filters, Aggregate, Time Window definitions.
C. Filters, Group By, Threshold definitions.
D. Filters, Threshold, Time Window definitions.
Answer: A
Explanation:
A subpattern in FortiSIEM is defined using Filters to match specific events, Aggregate conditions to apply statistical thresholds (e.g., COUNT), and Group By attributes to segment data for evaluation. These three components collectively determine how the subpattern functions.
NEW QUESTION 3
How can you query the configuration management database (CMDB) in an analytics search?
A. Click Value –> Select from CMDB.
B. On the CMDB tab, select an entry, and then click Create Search.
C. On the Admin tab, click CMDB Search.
D. Click Attribute –> Select from CMDB.
Answer: A
Explanation:
In an analytics search, you can query the CMDB by clicking Value –> Select from CMDB, which allows you to choose values directly from CMDB entries for the selected attribute, enabling precise filtering based on asset data.
NEW QUESTION 4
When configuring anomaly detection machine learning, in which step must you select the fields to analyze?
A. Design
B. Schedule
C. Prepare Data
D. Train
Answer: C
Explanation:
In the Prepare Data step of configuring anomaly detection in FortiSIEM, you must select the fields to analyze. This step defines the input features that the machine learning model will evaluate during training and detection.
NEW QUESTION 5
Which information can FortiSIEM retrieve from FortiClient EMS through an API connection?
A. Host software versions.
B. FortiSIEM license.
C. Host login credentials.
D. ZTNA tags.
Answer: D
Explanation:
FortiSIEM can retrieve ZTNA tags from FortiClient EMS through an API connection, enabling dynamic user and device classification for policy enforcement and incident response.
NEW QUESTION 6
How does FortiSIEM update the incident table if a performance rule triggers repeatedly?
A. FortiSIEM changes the incident status to Repeated, and updates the Last Seen timestamp.
B. FortiSIEM updates the Incident Count value and Last Seen timestamp.
C. FortiSIEM generates a new incident based on the Rule Frequency value, and updates the First Seen and Last Seen timestamps.
D. FortiSIEM generates a new incident each time the rule triggers, and updates the First Seen and Last Seen timestamps.
Answer: B
Explanation:
When a performance rule triggers repeatedly, FortiSIEM updates the existing incident by incrementing the Incident Count and refreshing the Last Seen timestamp. This avoids flooding the incident table with duplicates while still tracking repeated occurrences.
NEW QUESTION 7
Which statement about thresholds is true?
A. FortiSIEM uses fixed, hardcoded global and device thresholds for all performance metrics.
B. FortiSIEM uses only device thresholds for security metrics.
C. FortiSIEM uses global and per device thresholds for performance metrics.
D. FortiSIEM uses only global thresholds for performance metrics.
Answer: C
Explanation:
FortiSIEM evaluates performance metrics against both global thresholds, which apply system-wide, and per-device thresholds, which can be customized for individual devices. This dual approach allows flexibility in monitoring while ensuring consistent baseline alerting.
NEW QUESTION 8
Which running mode takes the most time to perform machine learning tasks?
A. Local auto.
B. Local.
C. Forecasting.
D. Regression.
Answer: B
Explanation:
In Local mode, FortiSIEM performs machine learning tasks using the full dataset without optimization shortcuts, making it the most time-consuming mode compared to Local Auto, Forecasting, or Regression.
NEW QUESTION 9
Which analytics search can be used to apply a user and entity behavior analytics (UEBA) tag to an event for a failed login by the user JSmith?
A. User = smith.
B. Username NOT END WITH jsmith.
C. User IS jsmith.
D. Username CONTAIN smit.
Answer: C
Explanation:
The correct syntax to match an exact username in FortiSIEM analytics search is User IS jsmith. This ensures that the UEBA tag is applied only when the event is specifically tied to the user “jsmith”, which is required for accurate behavioral analytics.
NEW QUESTION 10
Which two settings must you configure to allow FortiSIEM to apply tags to devices in FortiClient EMS? (Choose two.)
A. FortiEMS API credentials defined on FortiSIEM.
B. Remediation script configured.
C. ZTNA tags defined on FortiSIEM.
D. FortiSIEM API credentials defined on FortiEMS.
Answer: AD
Explanation:
To allow FortiSIEM to apply tags to devices in FortiClient EMS, FortiEMS API credentials must be defined on FortiSIEM to enable communication with EMS, and FortiSIEM API credentials must be defined on FortiEMS to allow EMS to accept tagging instructions from FortiSIEM. This bidirectional API trust is essential for tag application.
NEW QUESTION 11
What are two required components of a rule? (Choose two.)
A. Exception policy.
B. Subpattern.
C. Detection Technology.
D. Clear policy.
Answer: BC
Explanation:
A Subpattern defines the specific conditions or event patterns the rule is designed to detect, and the Detection Technology specifies the type of detection logic (e.g., real-time, historical). Both are essential for a rule to function in FortiSIEM.
NEW QUESTION 12
Refer to the exhibit:
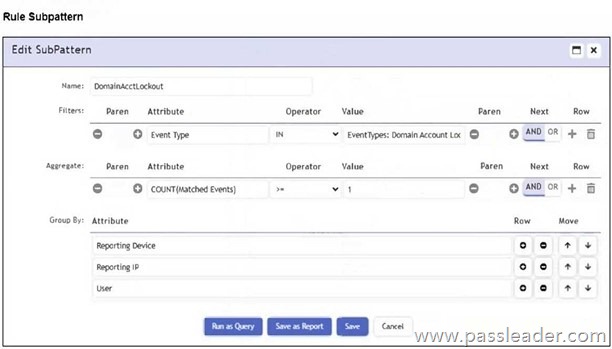
Which section contains the subpattern configuration that determines how many matching events are needed to trigger the rule?
A. Aggregate
B. Group By
C. Actions
D. Filters
Answer: A
Explanation:
The Aggregate section contains the condition COUNT(Matched Events) >= 1, which defines how many events must match the filter criteria for the rule to trigger. This is the subpattern configuration that determines the event threshold.
NEW QUESTION 13
Refer to the exhibit:
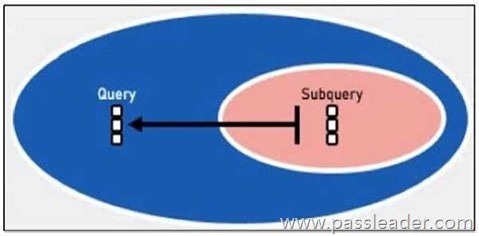
Which two lookup types can you reference as the subquery in a nested analytics query? (Choose two.)
A. LDAP Query
B. CMDB Query
C. SNMP Query
D. Event Query
Answer: BD
Explanation:
In FortiSIEM nested analytics queries, you can reference both CMDB Queries and Event Queries as subqueries. These allow correlation between CMDB data and event data for advanced detection use cases.
NEW QUESTION 14
Refer to the exhibit:
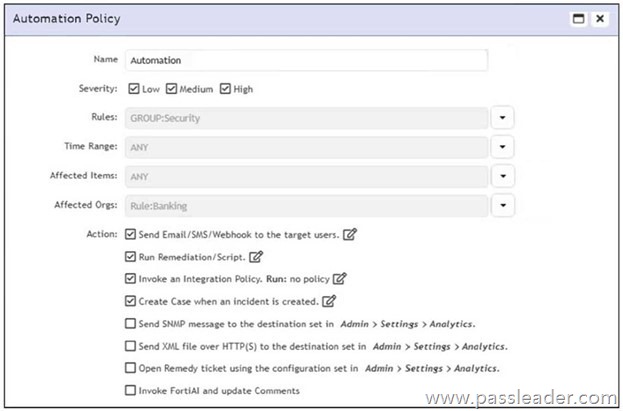
According to the automation policy configuration shown in the exhibit, what happens if an associated rule triggers?
A. FortiSIEM runs the remediation script, because that takes precedence over all other options.
B. FortiSIEM performs all selected actions.
C. FortiSIEM fails to the integration policy, because no policy is defined.
D. FortiSIEM sends an email, because that is first on the list.
Answer: B
Explanation:
When an associated rule triggers, FortiSIEM performs all selected actions in the automation policy. In this case, it will send an email/SMS/webhook, run the remediation script, invoke the integration policy (even if none is currently defined), and create a case. All checked actions are executed.
NEW QUESTION 15
Refer to the exhibit:
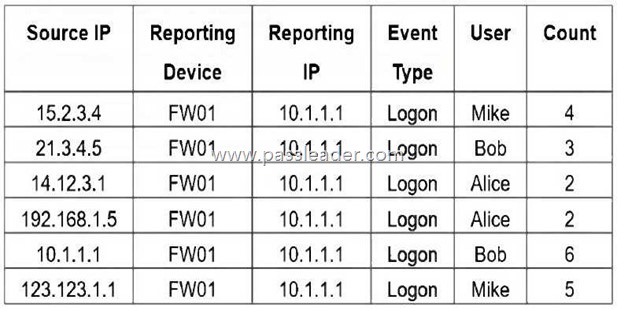
If you group the events by User, Source IP, and Count attributes, how many results will FortiSIEM display?
A. Two
B. Six
C. Three
D. Five
E. Four
Answer: B
Explanation:
Grouping by User, Source IP, and Count means that each unique combination of those three attributes will be treated as a separate result. In the table, all six rows have distinct combinations of User, Source IP, and Count – so FortiSIEM will display 6 results.
NEW QUESTION 16
……
Learning the PassLeader FCP_FSM_AN-7.2 dumps with VCE and PDF for 100% passing Fortinet certification — https://www.passleader.com/fcp-fsm-an-7-2.html (42 Q&As Dumps)
BONUS!!! Download part of PassLeader FCP_FSM_AN-7.2 dumps for free — https://drive.google.com/drive/folders/1N_fTofCvnsvQtf81GrH6Zts-VjBXOe2Y